Exploring the Porta Cipher: A Comprehensive Guide, 2023, by Karthikeyan Nagaraj
4.5 (138) · € 17.99 · In Magazzino

Exploring the Porta Cipher: A Comprehensive Guide | 2023. Understanding the Features, Encryption Process, Decryption Process, and Use Cases of the Porta Cipher | Karthikeyan Nagaraj.

Route Cipher: A Comprehensive Guide to Encryption and Decryption, 2023, by Karthikeyan Nagaraj

PRIYA GHOSH - Cognizant
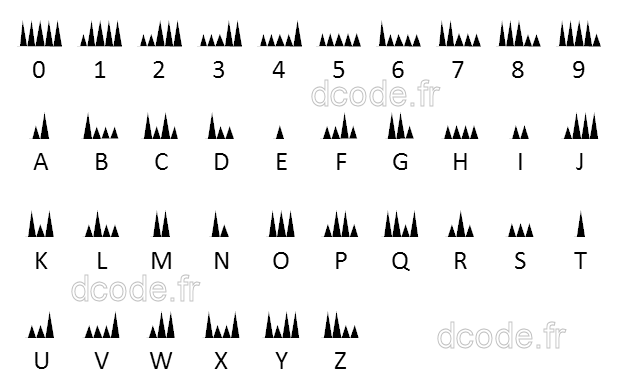
Understanding the Fractionated Morse Cipher: A Comprehensive Guide, 2023, by Karthikeyan Nagaraj

Understanding the Atbash Cipher: A Simple and Effective Encryption Method, 2023, by Karthikeyan Nagaraj

Zero Trust Architecture: A Comprehensive Guide to Reinventing Cybersecurity, Karthikeyan Nagaraj, by Karthikeyan Nagaraj
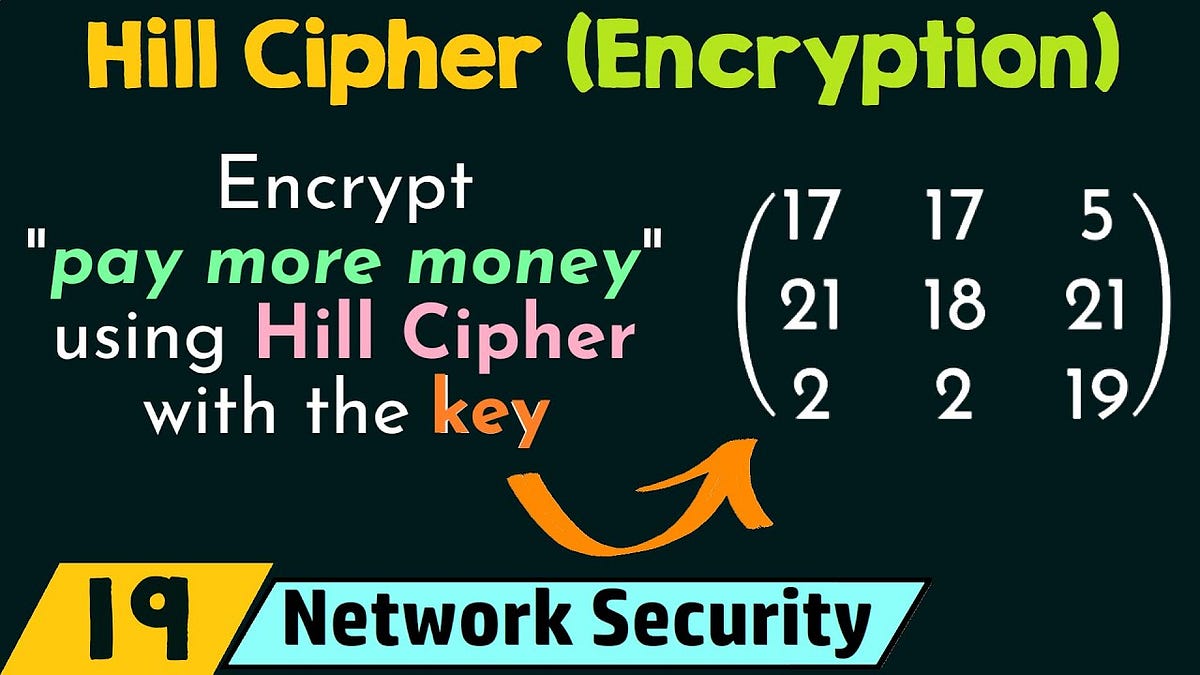
Understanding Hill Cipher: A Comprehensive Guide, 2023, by Karthikeyan Nagaraj

Anubis Encryption: Understanding the Key Concepts, 2023, by Karthikeyan Nagaraj
PDF) SPIRAL: Extreme Performance Portability

CISSP (ISC) 2certification Practice Exams and Tests by Jordan, Ted, PDF, Security
Building a Secure Mobile App in the Cloud, by Boris Zaikin
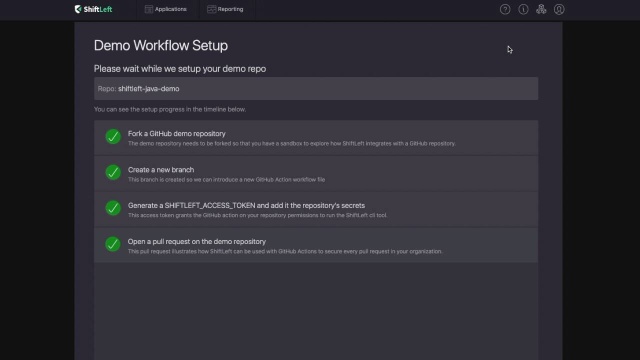
Finding Sensitive Data Leaks In Code Using ShiftLeft CORE, by Vickie Li







