Novel Attack Turns Devices Against Themselves
4.6 (662) · € 35.99 · In Magazzino

Researchers have discovered how to remotely manipulate the Echo through its own speakers.

Phishing Scams: How to Protect Yourself, IdentityForce®

Jonathan Swift, Satirist, Poet & Clergyman

The Death of a Gun-Rights Warrior - The Atlantic

Tarring and feathering - Wikipedia

Top 5 Risks Facing Student (& Schools) on Chromebooks

Zero-Day Exploits & Zero-Day Attacks

Legendborn, Book by Tracy Deonn, Official Publisher Page

The Turner Diaries - Wikipedia
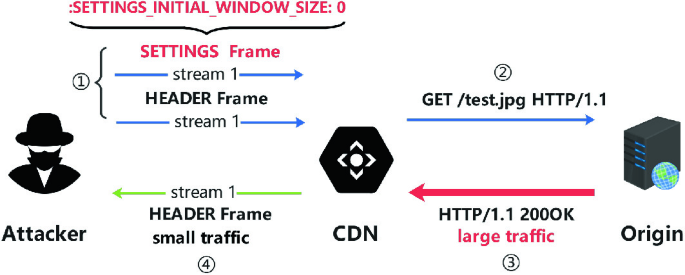
Two Types of Novel DoS Attacks Against CDNs Based on HTTP/2 Flow Control Mechanism

Apple's iOS 17.3 Stolen Device Protection Update Aims to Stop iPhone Thieves - WSJ
Potrebbe piacerti anche







